
Who?
Whalebone offers an IT security solution designed to protect businesses from online threats such as malware, ransomware and phishing attacks.
What?
Protects against cyber threats with protective DNS Immunity
Blocks malicious domains and gets rid of unwanted traffic
Protects all devices without the need to install software
Includes Identity Protection and off-net protection
Advantages?
Immediate safety for all users and devices
No installation, all devices are protected
No maintenance or additional personnel required
What is Whalebone Immunity?
Whalebone Immunity provides businesses and institutions with an essential layer of protection – a complete control over the DNS traffic regardless of size or complexity of their network. More than 90% of malware uses DNS resolution at some point during its life cycle, so in this layer you can stop attack strategies which elude firewall, end-point protection, and other traditional protection methods.
The majority of organisations still do not have direct control over their DNS resolution, nor do they monitor and filter their DNS traffic. This makes them vulnerable to:
- DNS tunneling, which is used to extract data from the network or to smuggle a malicious code. It was used for example in one of the biggest attacks of our time – the SolarWinds attack, which affected over 18,000 companies and institutions, including Microsoft, Cisco, and parts of the Pentagon.
- DGA (domain generation algorithms), which are used to create random domains used for communication with malware in the targeted network, since the traditional methods rely on threat intelligence databases.
- Malware delivered by supply-chain attacks, IoT attacks, and more, since those ways usually elude the standard security stack. Nevertheless all of the devices need to use DNS resolution and can be thus protected at this layer.
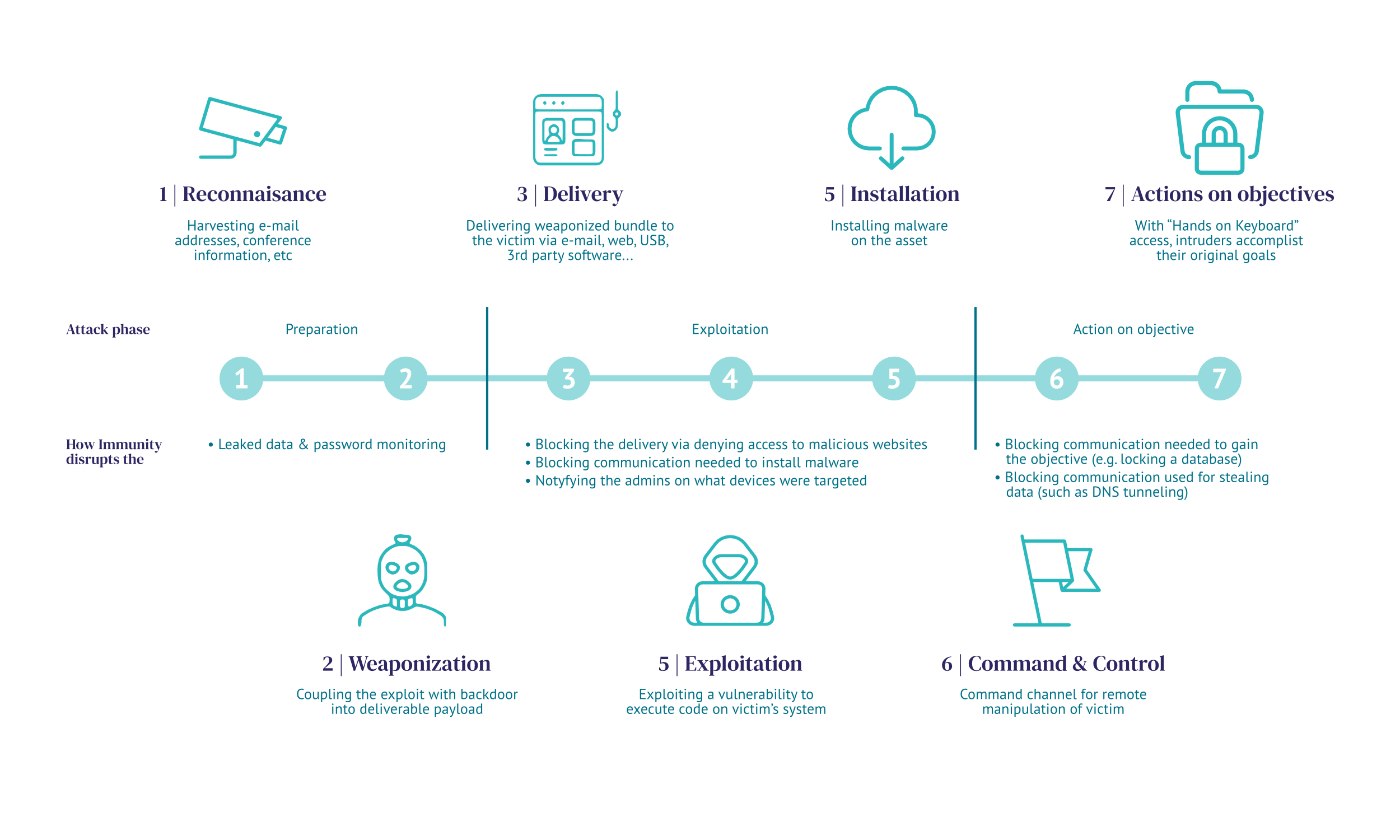
Why is DNS security essential?
When it comes to DNS resolution, firewalls just look at the individual DNS queries to identify threats, and are therefore reliant on databases of known codes used for abovementioned tactics. Whalebone analyses patterns using AI which allows it to distinguish behaviour connected to DNS tunneling, DGAs, and wide range of malware, stopping even the threats which are not a part of any database yet (0-day threats).
Moreover, additional features of Whalebone Immunity ensure coverage of other blind spots in the standard security stack:
- Homograph attacks alerting lets the admins know if a domain similar to the company domain (such as one using Greek letters to mimic the original domain) is used to communicate with the network. This is a popular way to lure credentials out of well-meaning users.
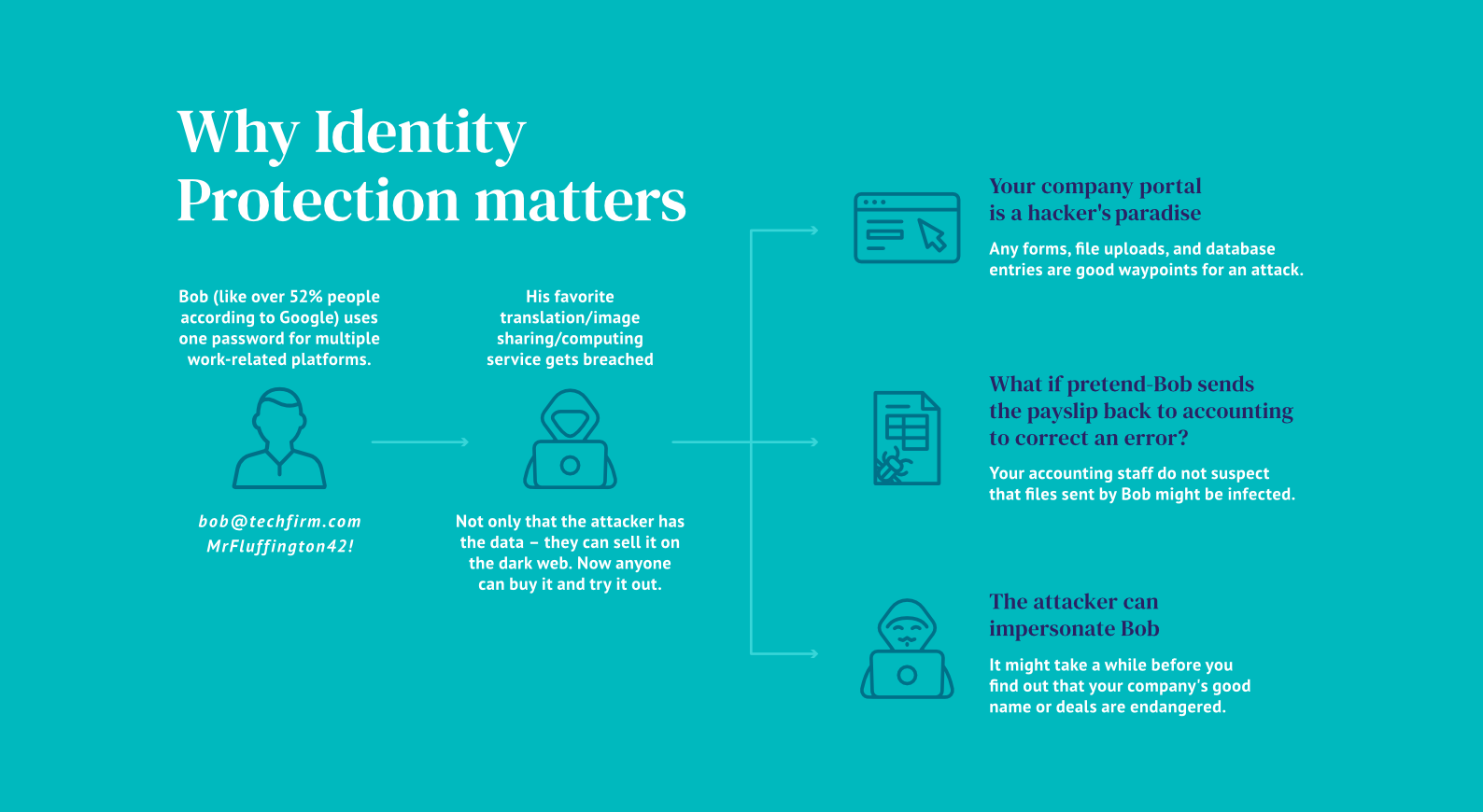
- Identity protection alerts the admins of all identified leaks of sensitive information connected to the company domains – such as passwords and login credentials which leaked during breaches of 3rd party services. Even solid companies like Adobe, Canva, LinkedIn and other were breached in past and the stolen credentials are routinely sold on the Dark Web. This feature identifies such leaks in over 50% of Whalebone’s clients.
- Home Office protection allows the protection of any device with a simple app, without all of the hustle which is connected with using VPN – redirecting the DNS traffic to the resolver means smooth experience and no need to set-up additional policies and processes.
To sum up, without DNS protection, there are multiple blind spots in the security perimeter. Moreover, thanks to not needing installation in the end devices, Immunity does not require almost any maintenance and thus saves your IT team time and resources. And last but not leads, it adds a security layer to gain maximum confidence that the network is as protected as possible in case there is any malfunction or insufficient threat intelligence in the other security layers.
Find a detailed list of key elements below:
- Protection against man-in-the-middle, DNS tunnelling, C&C, DGA, phishing, spearphishing, homograph attacks, botnets, coinminers, IoT attacks, ransomware, and all stages of malware in general…
- DNS FW & network segmentation, SIEM/Log mngmt,
Office365 & MS Azure, endpoint, anomaly detection, DHCP - DNSSEC — SMTP (e-mail) and HTTP/HTTPS (web)communication
- Home office security — protect even your employees online or on a business trip
- Content filtering — gambling, violence, torrenting, cryptomining, adult content…
- Identity protection — identify old and new leaked credentials, passwords, keycard codes…
Deployment and immediate results
Whalebone Immunity – a fast and stable recursive DNS resolver with sophisticated security modules – is scalable and fits network of any size, be it smaller companies or enterprises with multiple sites and international branches. Usually the cloud version can be up and running in 1 hour, after which the whole network including computers, mobile phones, cameras, servers, printers, and any other IoT devices is immediately protected.
For the easiest and fastest deployment there is a cloud version of Whalebone Immunity, while on-premise deployment offers deeper insight into the DNS traffic up to the level of a single device, which allows to pinpoint exactly which device or user was targeted. Usually, the on-premise deployment takes up to 4 hours to deploy, after which the whole network including any device connected to the internet is immediately protected.
The free trial version lasts 30 days, during which the full functionality, including the Identity protection feature, is available. Around 50% of customers find out that there is malicious traffic not blocked by their other security stack during the trial version, and around 50% of customers identify a leaked sensitive data using the Identity protection feature.
Find out how Whalebone Immunity saves your time and effort here.
Unique threat intelligence to identify cyber attacks
Apart from the standard threat intelligence sources (public and paid databases and threat intelligence feeds), Whalebone utilizes unique measures to ensure that any threat is identified and filtered on DNS level as soon as possible:
- AI engine analyzing patterns identifies DGAs, DNS tunneling, and suspicious patterns in the DNS traffic to cover the blind spots of other security layers
- MISP threat intelligence exchange within DNS4EU connects local Cybersecurity Emergency Response Teams (CERTS) with the members of the DNS4EU consortium, ensuring that immediately after identification of a local threat, the information is pushed into the shared database. Given that local threats in EU countries are not often a focus of international Threat Intelligence databases, this adds unique and highly specific data to the mix.
- Data from the attacks on Whalebone’s telco partners’ users provide an unique source of both local and global threats which are targeting people and institutions who are clients of both small and big telco companies.
About Whalebone
The goal of Whalebone is to protect 1 billion people worldwide. It is a global leader in telco consumer security, one of 25 fastest growing companies in Central Europe, and a leader of the DNS4EU consortium which was hand-picked by the European Commission to develop and operate an official DNS resolver for the European Union.


