
23 Mar How to stop cybercriminals misusing privileged credentials
Market analysts rank securing privileged access as the no. 1 priority for CISOs due to high-profile breaches focused on privileged accounts. Major cyber-attacks in recent years have all had one thing in common: the breach was the result of the misuse or abuse of privileged accounts.
You need a trusted Privileged Access Management* (PAM) solution to keep potential data breaches at bay (and reduce the headache of managing accounts yourself). More than 85% of organisations say their employees have more privileges than they need. This is a huge security risk for most organisations, including yours.
*Privileged Access Management (PAM), sometimes referred to as ‘privileged account management’
What is a privileged account?
Privileged accounts are a subset of accounts that provide elevated access and permissions across applications, devices and systems within an IT environment.
Examples of common privileged accounts include the UNIX root account, the Active Directory administrator account, a DBA account, or the superuser accounts built into every application and system.
What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is the set of cybersecurity strategies and technologies used to control the elevated (‘privileged’) access and permissions for users, accounts, processes and systems in an IT environment.
Why is Privileged Access Management (PAM) important?
Hackers are targeting your privileged accounts, which provide unrestricted access to your systems and data. In almost every recent high-profile breach, lapses in security and user practices were exploited by hackers to gain privileged account credentials. By implementing the right level of privileged access controls, PAM can help organisations condense their attack surface and prevent or at least mitigate the damage from both external attacks and insider misuse or negligence.
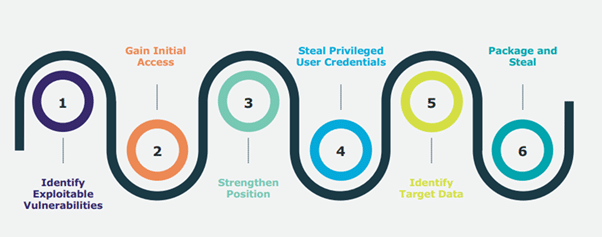
But you can limit your vulnerability with an on-demand solution that provides a secure, efficient and compliant way to manage privileged accounts:
One Identity Safeguard On Demand automates, controls and secures the provision of privileged credentials with role-based access management and automated workflows.
Why consider our on-demand (SaaS) solution?
- Accessible: Runs in an internet browser from any device
- Cost-effective: No upfront hardware costs and flexible payment options such as pay-as-you-go models
- Easy to manage: No installation, device updates or traditional license management
- Easy to use: Requires no changes to user workflows (works in transparent mode)
- Accreditation: One Identity SaaS solutions are developed, operated and supported within the One Identity Information Security Management Platform, which is ISO/IEC 27001:2013 certified.
Try One Identity Safeguard virtually for free!
Start your trial to see how Safeguard can help you. Prevent and limit the damage from a breach with this SaaS-based PAM solution that provides a secure, efficient and compliant way to manage privileged accounts. Safeguard On Demand combines a secure password safe, session management and a monitoring solution delivered from the cloud.
- Mitigate the potential damage of security breaches
- Meet compliance requirements
- Realise rapid ROI with simplified deployment and management
- Deploy in transparent mode with no changes to user tools or workflows
- Automate time-consuming privileged account processes
- Approve password requests from anywhere
- Monitor, record and audit sessions with real-time alerting and blocking
- Use pattern-free analysis to identify poor user behavior
- Reduce alert noise by categorising alerts by risk and deviation level



No Comments