
18 Feb Enhancing Cybersecurity through Asset Discovery and Vulnerability detection
Introduction
In an era where cyber threats are growing exponentially, organizations face the daunting challenge of securing ever-expanding attack surfaces. With the proliferation of Internet of Things (IoT) devices, cloud environments, and remote work infrastructures, traditional cybersecurity solutions often fall short in providing comprehensive visibility and control.
A lot of companies don’t have a clue about which devices are connected to the network. The network is the backbone of the company, it connects users and devices with each other and with the Internet. It is so useful, as providing network connecitivty expands possibilities in terms of automation and work efficiency. However, this also enlarges the risk to be vulnerable against cyber attacks.
That’s why tools which enable asset visibility and vulnerability detection are so important to have a place in the cybersecurity strategy of a company. Everything starts with the question “What’s in our network”. By answering this question, a company can start it’s plan to protect these devices in the right way.
Within the Kappa Data portfolio, two groundbreaking solutions revolutionize how organizations approach asset visibility, threat detection and network protection.
What does such a solution do?
Both Armis and runZero share a unified mission: to provide organizations with complete visibility into their network environments and to protect them from vulnerabilities and threats. The core objective is to ensure that every device, whether managed or unmanaged, is accounted for and secured against modern cyber risks. This shared vision focuses on:
- Visibility across the attack surface: Identifying and understanding all connected assets, including IoT devices, shadow IT Components, and other unmanaged endpoints
- Risk Mitigation: Proactively detecting vulnerabilities and suspicious behavior to prevent breaches
- Operational Continuity: Strengthening security without disrupting business operations. OT environments can be really fragile, so scanning and detection should work in the background without interrupting OT business continuity
While their approaches and focus in terms of verticals may differ, both solutions aim to empower organizations to build resilient cybersecurity frameworks that adapt to evolving threats.
Armis: Enterprise-Grade Asset and Traffic Anomaly Detection
Armis is an enterprise solution tailored for securing unmanaged and IoT devices, with a particular strength in critical sectors like healthcare and hospitals. Its platform constantly analyzes network traffic, identifying anomalies and threats in real time to protect connected assets and ensure operational security.
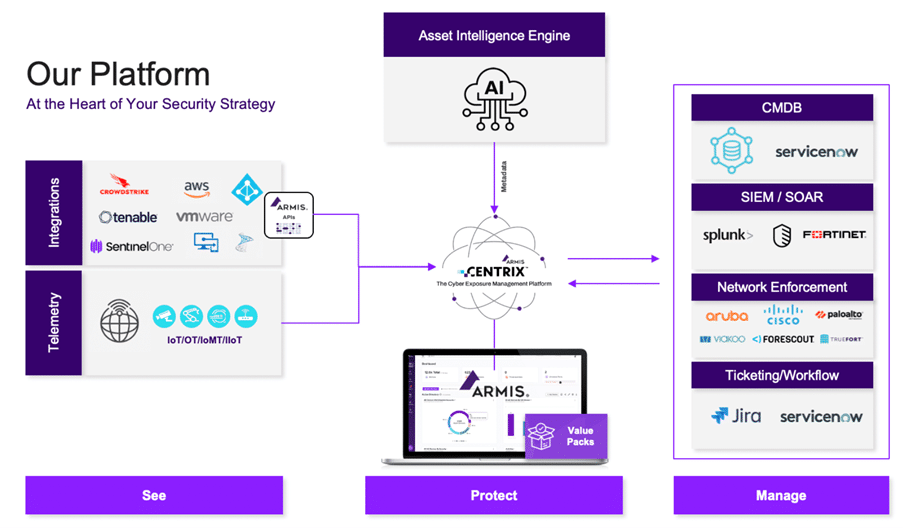
Where Armis really stands out is:
- Medical and IoT Device Protection: Secures medical devices such as infusion pumps, MRI machines and industrial IoT systems
- Traffic Anomaly Detection: Continuously monitors network traffic, analyzing source and destination behavior to detect malicious and suspicious activity. This includes known signature-based threats like Log4j and SQL injection, as well as behavioral pattern analysis for brute force attacks, port scans, malicious host connections, and abnormal asset behavior
- Global Threat Intelligence Integration: Correlates data with threat intelligence to preemptively identify and mitigate risks
runZero
runZero, formerly known as Rumble, specializes in discovering and cataloging every device connected to a network. It provides organizations with detailed, real-time insights into all assets, including IoT devices, unmanaged endpoints, and shadow IT components. By leveraging non-intrusive scanning methods, runZero ensures full visibility without disrupting network operations.
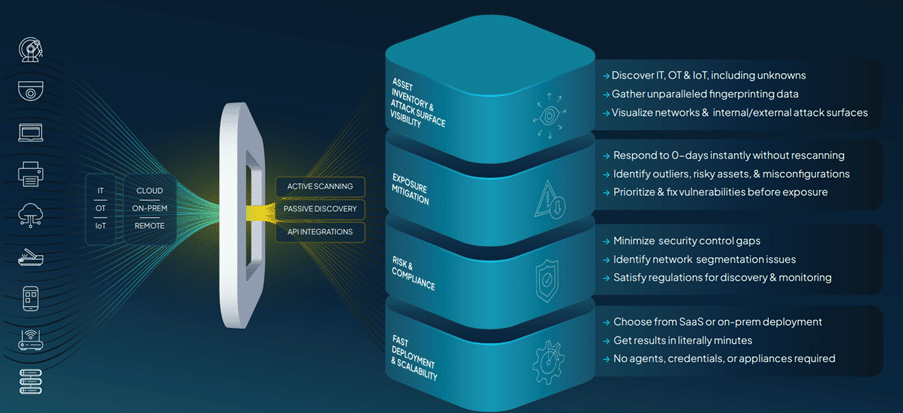
Discovering these assets should be done in different ways, that’s for sure. runZero is therefore capable to recognize, discover and get insights about these assets in different ways:
- Agentless Discovery: runZero works completely agentless. While other solutions sometimes work with agents that need to be deployed on the assets, runZero scans the network without manual intervention
- Detailed Asset Inventory: runZero discovers devices through active scanning, passive discovery and API integrations. This way runZero can get detailed information about assets including operating systems, services and vulnerabilities.
- Seamless deployment: runZero is quick to setup and offers an intuitive interface for teams of all sizes
Why Are These Solutions Necessary?
The cybersecurity landscape is shifting rapidly: As organizations adopt more connected devices and move to hybrid environments, gaps in traditional security frameworks become evident. Here’s why solutions like Armis and runZero are critical:
- Rising IoT Adoption: Gartner predicts there will be over 25 billion IoT devices by 2030, many of which lack built-in security.
- Shadow IT Proliferation: Employees, contractors, third party companies often connect unauthorized devices to networks, creating blind spots. For example runZero claims that 25% of assets (on average) found by them are previously unknown to enterprise customers. Even a lot of devices that should work air-gapped, are exposed to the Internet in some way.
- Sophisticated Threats: Cybercriminals increasingly target unmanaged and IoT devices as easy entry points
Armis and runZero address these challenges by providing visibility, control and protection for every connected device.
How These Solutions Improve Overall Cybersecurity
It’s clear what the solutions do, but what does it offer in terms of cybersecurity improvement?
These solutions make sure that you know what’s in your network. Knowing what’s on your network is the foundation of any security strategy. Armis and runZero ensure nothing goes unnoticed, and appropriate security measurements (such as EDR, NAC,…) can be taken. They use advanced algorithms and threat intelligence to identify vulnerabilities and anomalous behavior.
The current time requires companies to meet compliance and governance. Comprehensive asset management simplifies meeting regulatory requirements.
By automating asset discovery and threat detection, organizations can focus on strategic initiatives.
Integration with Other Vendors and Products
The true power of these platforms lies in their ability to integrate with leading cybersecurity and network management solutions. Here are some examples:
- Network Access Control: The moment you find a device that shouldn’t be active in a certain network, Network Access Control can be triggered to create rulesets that assign these assets to dedicated network segments
- IP Address Management (IPAM): In a lot of companies, an IP Address Management solution keeps track of assigned IP addresses, assets and networks. These solutions can make sure that IP Address Management can be simplified
- XDR/MDR: An endpoint protection solution provides real-time visibility of managed devices, where the integration of both solutions can fill the gap between what’s managed and unmanaged to unify threat response across both types of devices
- Other SIEM and SOAR Platforms: Feeds detailed asset and threat data into security information and event management (SIEM) and security orchestration, automation and response (SOAR) platforms for streamlined incident response.
Conclusion
Asset discovery and vulnerability management platforms represent the next generation of cybersecurity solutions, addressing critical visibility and protection gaps in today’s complex IT environments. Every Cybersecurity Journey starts with grasping what lives in the company’s network before being able to protect the environment in the best way possible.
By integrating with other leading vendors, these platforms empower organizations to build robust, scalable, and proactive security ecosystems. As cyber threats continue to evolve, adopting innovative solutions like Armis and runZero is no longer optional.
In terms of next steps, if you are interested in these kind of solutions, subscribe on the free trial of runZero via https://runzero.com/try/ and certainly contact [email protected] for more information or to set up a Proof of Value with Armis.



No Comments